
Innovation must dare you
A New Year greeting where people get their refreshers from in the New Year, Scheveningen and a fresh dive take to obtain new insights. That the ball is orange cannot be a coincidence…
Back in time…
A several years ago (in 2003, to be exact) I created server manage support.
SBS were in my eyes a beautiful solution where the management was configured, where you run everything on a single server (yes even active directory) and where wizards took the owner much out of their hands. The idea of a ” SYSTEM ” What took off everything what was complex and costly and resulted in what where the owner wanted to pay for that functionality.
Stuxnet
A good example of what hang over in 2010 when the first computer virus on the market was also what Programmer Logical Controllers could infect. Granted if you turned no nuclear centrifuges in Iran on Siemens then there was little to fear, but it gave you to think that this also could occurred at this level threat.

At that time was the only antivirus protection for SCADA systems, something that is now outdated and not protective. A useless checkbox exercise, according to a Google security official –http://bit.ly/2fzE5iP. Under the push of a firewall again this time industrial firewalls were highlighted by industrial control suppliers, the assumption was that would keep and stop these attacks.
We saw from an IT thought that in addition to the fact that IT firewalls itself are sensitive to security vulnerabilities and this can be used to all companies to access to and from the cloud to a huge challenge to critical infrastructure systems that use even hardcoded passwords.
GROUND ZERO
So if you are from the ground would have to build an identity and access system how do you deal with authentication, remote access, and protect against vulnerabilities in a rapidly changing environment with Big Data, IOT and compliance requirements as GDPR?
Protection-If you now allow access to only authorized users and unauthorized users from love? Then you can be flexible without worrying of the threats that are coming in daily.
Access and Compliant What if you can see who has business with you and those who do may “guide” to the asset itself, but only those asset / data repository and nowhere else?
Legacy support – that f you have systems who are still working fine not have to replace because there are no security updates available anymore?
In control– What if you assign yourself passwords but do not need to share them with people inside or outside the organization?

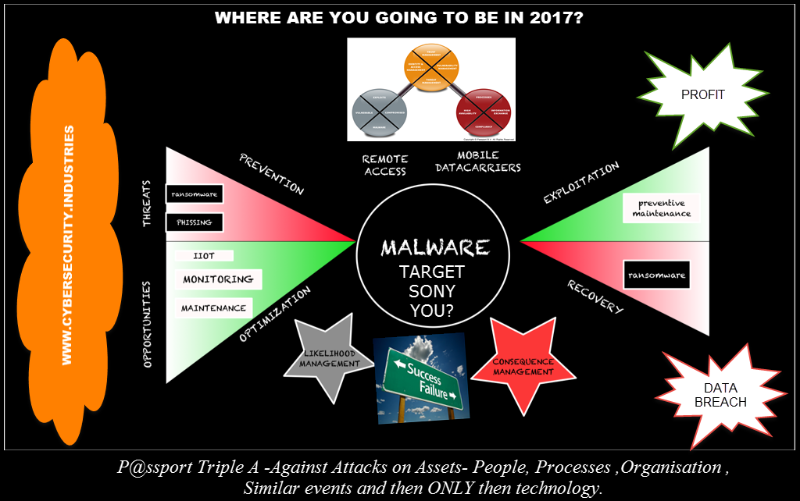
P@ssport went to work and used the ADM circle from Togaf also to ensure that this reasoning Triple A -Against Attacks on Assets found a connection to management, system owners and network administrators. Then, in the sought within E-circle solution components that had to meet four requirements:
Simple, Compatible, Preventive, Affordable.
Wrong way

Fog of More
At that time, there were other companies with “next generation” security, where the innovativeness depends on yet another heuristic database, just turn the scanner on the device itself, a typical reactive action that also does not work at the moment that tunnel through the device is set up.
There were ids, ips and everything you can find above where we mainly to the reactive side, which is the figure on the right after the assets are infected. The idea that protection occurs on the right side is thus shown that this is nonsense. Antivirus protection is actually Anti Virus analysis After all, the file is already on the device where you want it!
Like a lot of disclaimers go back to premium prices, complexity, and again hope that the components work well together (encryption, two factor authentication, directory services, tokens) believe that the partners have well established their components (weather monitoring data center, shared virtual environments, applications with personal data) and you do not understand otherwise we are certified iSO 27.xxx and reactive “colored” reports.

Where recruiters still find it important that you have to be VMware certified while a complete Oracle database you have virtually running within half an hour from the cloud.
Granted, we have come far from the first hard drive.

A bit like we did indicate we have made the hard disk smaller and now we need not require a forklift and a pallet, but the operation remains the same. It is the will to change important is it not to linger on Dogmatism…

Securing companies is a game, the greatest game in the world if you know how to play it.
Peter Rus
Innovative Capability
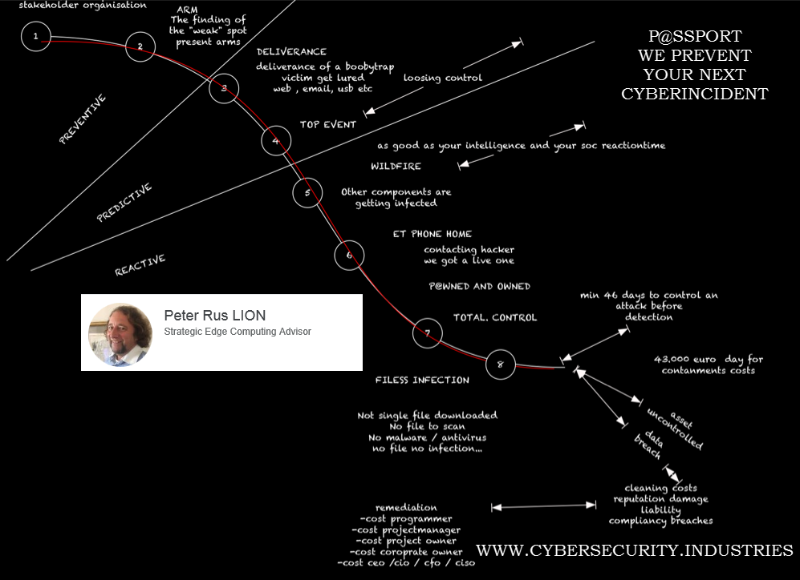
It takes 229 days to detect malware and an average of $ 3.5m for reactive repair the damage and innovative companies get started with sandboxes, we went six years ago to work with on time, to intervene preventively.
Triple A has the complete elimination of the complex security legacy stack made possible and has 4 columns.
- Identify- who knows why when needs access
- Monitor who knows where why and how access
- PROTECT, protect your assets against zero exploits, third-party and legacy systems
- Audit know to the smallest letter what has changed, and can provide access in line with GDPR to data and assets without privacy issues. Something that 46% of businesses are not ready for.
Triple A Preventive Cyber Risk management
P@ssport a preventive approach and looks at how you can prevent an undesirable situation. Prevent is better than to cure, and we do what others leave. we engage in cyber kill chain, namely at level 2.
Similar anti-virus and anti-malware intervenes 5, and if you just failed your SOC yet to stop the rampant virus, reactive and probably too late.
Bridging the GAP
Follow the red reactive thread: Something the current security solutions cannot match because of the tunnels and the latest emerging threat “file less infection” After all, if a file is downloaded, so there is no file to scan shows the anti-malware and antivirus no file. No file no infection..
in Control
As always runs in a 24/7 economy accessibility and safe and secure work, something we have been doing since 2012. So you want to be doing to optimize your business processes, which saves money and self are in control?

Where you can omit reactive work such as the making of reports that are required from compliance, the “discovery” of malware on average 229 days and 3.5 million $ to repair the damage are all the result of risks overshooting too far with an additional compliancy requirements where a little more than half the is begun. www.linkedin.com/hp/update/6221630312636645376

P@ssport prevention without detection since 2012.

We did so, and bring protection without discovery.
And made a good system which beats a bad person every time.
A good system will beat a bad person every time.
P@ssport- Your hands cant hack what your eyes cant see.
Dr. Henk Jan Jansen

